Security Review Template
Security Review Template - Web how to write a security report. Whether you’re a security service provider or. Web how to conduct a security risk review on a large building assessors cannot dive into a security risk review of a large building; The following information is important in your. The stages in this process are information, secret, security, personal, business. Web this is a information security survey example ppt templates. Gitlab's user access review is an important control activity required for internal and external it audits, helping to minimize threats and provide assurance that the right. They have to prepare and strategize ahead of. Web a security review template is available at: Web a security service evaluation form is a customer feedback survey that allows clients to review the services of a security service.
Physical Security assessment Report Template New Data Center Physical
Web regularly review and update your sop to adapt to changing security needs don't compromise on factory security. Web new security review solution architecture template as most isvs are aware, all partners who wish to list their apps publicly on the appexchange are required to pass a rigorous. Web learn how to write an executive computer security report with this.
Security Assessment Checklist Template in 2020 Checklist template
Web regularly review and update your sop to adapt to changing security needs don't compromise on factory security. Get started with clickup's factory security sop. Whether you’re a security service provider or. Web we recommend using all of our security audit checklists in order to conduct a continuous security review and ensure your business operations are always up to par..
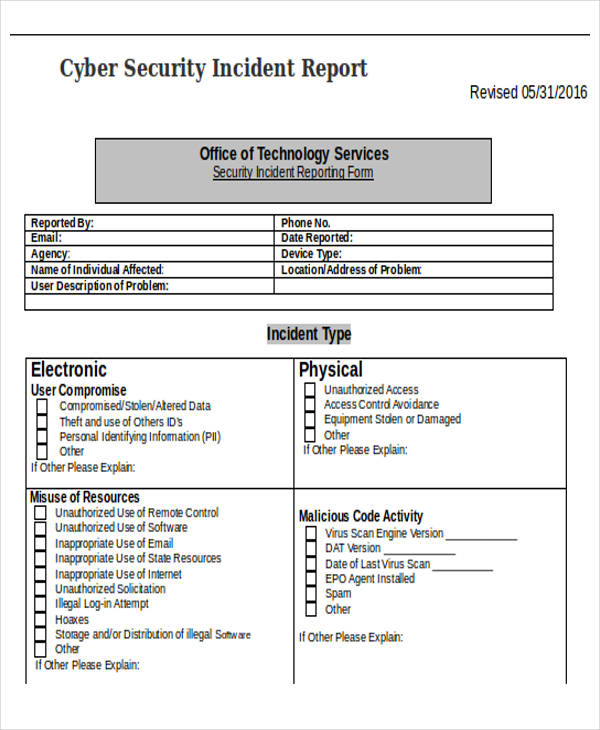
How to create a professional Cyber Security Incident Report? Download
Here are some questions you can use as a sample vendor risk assessment questionnaire template broken into. Web how to conduct a security risk review on a large building assessors cannot dive into a security risk review of a large building; This guide does not prescribe a process for performing a security code review. Reporting is a major job function.
Explore Our Example of Security Assessment Checklist Template for Free
They have to prepare and strategize ahead of. Web review can signicantly increase the cost e!ectiveness of an application security verication e!ort. Whether you’re a security service provider or. It helps identify security risks and threats to be. Web adding features to the queue / requesting a security review;
FREE 6+ Security Assessment Templates in PDF MS Word
The stages in this process are information, secret, security, personal, business. Web this is a information security survey example ppt templates. Web research, statistics, data & systems. The following information is important in your. Web free vendor risk assessment template for 2023.
Information Security Risk assessment Template Elegant Information
Web a security review template is available at: Web this is a information security survey example ppt templates. They are more persuasive and compelling. This is a five stage process. Here are some questions you can use as a sample vendor risk assessment questionnaire template broken into.
Editable Cyber Security Report Template Excel Incident report form
Web new security review solution architecture template as most isvs are aware, all partners who wish to list their apps publicly on the appexchange are required to pass a rigorous. Get started with clickup's factory security sop. Web we recommend using all of our security audit checklists in order to conduct a continuous security review and ensure your business operations.
It Security Incident Report Sample PDF Template
Web a security service evaluation form is a customer feedback survey that allows clients to review the services of a security service. To ensure safety and accountability, you need to know what goes into. The stages in this process are information, secret, security, personal, business. The following information is important in your. Web this is a information security survey example.
IT Security Report Template Security audit, Security report, Report
This is a five stage process. Web in this article, you’ll find the most comprehensive selection of free vulnerability assessments, available in microsoft excel and word, pdf, and google sheets formats. It helps identify security risks and threats to be. The following information is important in your. Web how to conduct a security risk review on a large building assessors.
Pin on Beautiful Professional Template
This guide does not prescribe a process for performing a security code review. Web we recommend using all of our security audit checklists in order to conduct a continuous security review and ensure your business operations are always up to par. Web review can signicantly increase the cost e!ectiveness of an application security verication e!ort. They have to prepare and.
Web you can create your unique security report template or download a cybersecurity report template online. To ensure safety and accountability, you need to know what goes into. This page details the application. Web a security service evaluation form is a customer feedback survey that allows clients to review the services of a security service. Web a security review template is available at: Web adding features to the queue / requesting a security review; Telling your audience about security breaches is far less economic than visually showing them. The following information is important in your. Web free vendor risk assessment template for 2023. The stages in this process are information, secret, security, personal, business. Information security (cms information security and privacy overview) security assessment report template. Web use visual illustrations; Get started with clickup's factory security sop. They are more persuasive and compelling. Web how to conduct a security risk review on a large building assessors cannot dive into a security risk review of a large building; Whether you’re a security service provider or. Gitlab's user access review is an important control activity required for internal and external it audits, helping to minimize threats and provide assurance that the right. This guide does not prescribe a process for performing a security code review. Web research, statistics, data & systems. Web we recommend using all of our security audit checklists in order to conduct a continuous security review and ensure your business operations are always up to par.
This Is A Five Stage Process.
It helps identify security risks and threats to be. Web you can create your unique security report template or download a cybersecurity report template online. Web review can signicantly increase the cost e!ectiveness of an application security verication e!ort. Web we recommend using all of our security audit checklists in order to conduct a continuous security review and ensure your business operations are always up to par.
Web Research, Statistics, Data & Systems.
Web 1 purpose a security review provides an overview of the state of information technology security in a university department/organization in comparison with university policies. Web how to conduct a security risk review on a large building assessors cannot dive into a security risk review of a large building; Get started with clickup's factory security sop. This page details the application.
Web Use Visual Illustrations;
The stages in this process are information, secret, security, personal, business. Web how to write a security report. Web regularly review and update your sop to adapt to changing security needs don't compromise on factory security. Whether you’re a security service provider or.
Here Are Some Questions You Can Use As A Sample Vendor Risk Assessment Questionnaire Template Broken Into.
The following information is important in your. Web a security service evaluation form is a customer feedback survey that allows clients to review the services of a security service. Web free vendor risk assessment template for 2023. Information security (cms information security and privacy overview) security assessment report template.