Secure Sdlc Policy Template
Secure Sdlc Policy Template - Web the guide focuses on the information security components of the sdlc. Concentrate on one piece at a time. Web michigan tech’s sdlc includes six phases, during which defined work products and documents are created, reviewed, refined, and approved. Within this policy, the software development lifecycle consists of. Web sdlc security control guidelines the sdlc process will adhere to the following information security controls: Web ciso has developed templates and provided samples for each task as well as a template for the overall information security plan. Refine that piece as much as possible and then move on to the next. One section summarizes the relationships between the sdlc and other information technology (it). A requirement specification document is. These templates along with samples can be.
Secure SDLC PowerPoint Template PPT Slides
1.1.1 opm sdlc policy opm it programs and projects must use an sdlc according to standards outlined in this document. Refine that piece as much as possible and then move on to the next. One section summarizes the relationships between the sdlc and other information technology (it). Web this sdlc is detailed in the ku systems development life cycle (sdlc).
SDLC Software Requirements (SRS) template Software Development
Recommendations for mitigating the risk of software vulnerabilities date published:. Web michigan tech’s sdlc includes six phases, during which defined work products and documents are created, reviewed, refined, and approved. Using this template assures a consistent level of. Web download the software development lifecycle policy template to provide your organization with a documented software development lifecycle that is to be.
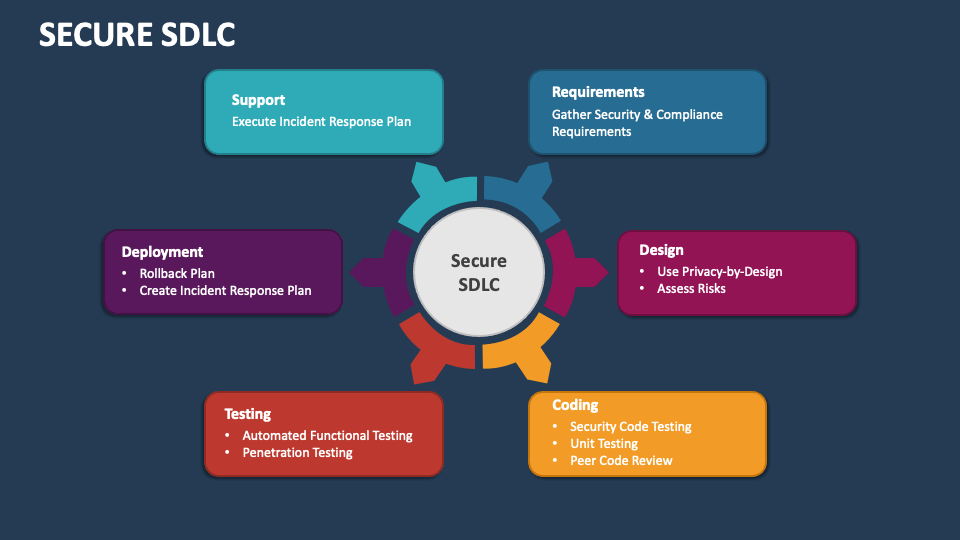
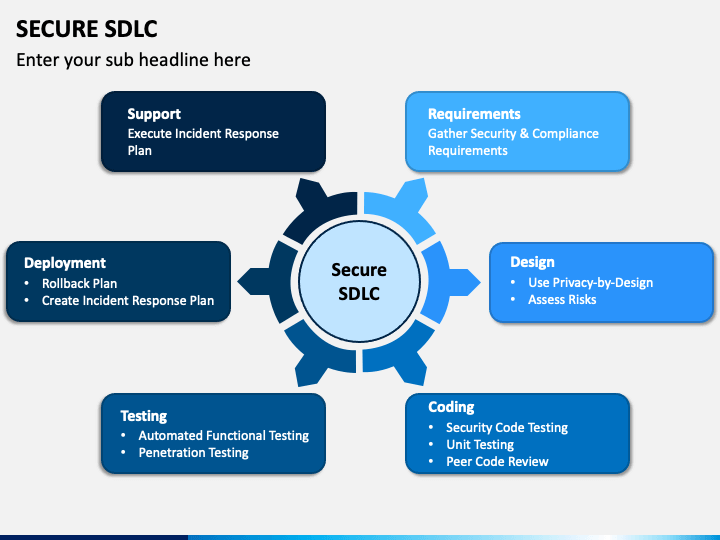
Information Security and the SDLC
Not every project will require. Web sdlc security control guidelines the sdlc process will adhere to the following information security controls: Web in a secure sdlc, a sponsor initiates this activity and the development team is responsible for security training. Recommendations for mitigating the risk of software vulnerabilities date published:. Refine that piece as much as possible and then move.
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Ensure that development team uses the security libraries available in the. Represent sdlc are inception, sequential elaboration, evolution of construction, an application transition, project. Using this template assures a consistent level of. Web security policy, a secure sdlc must be utilized in the development of all applications and systems. Web system development life cycle (sdlc) phases.
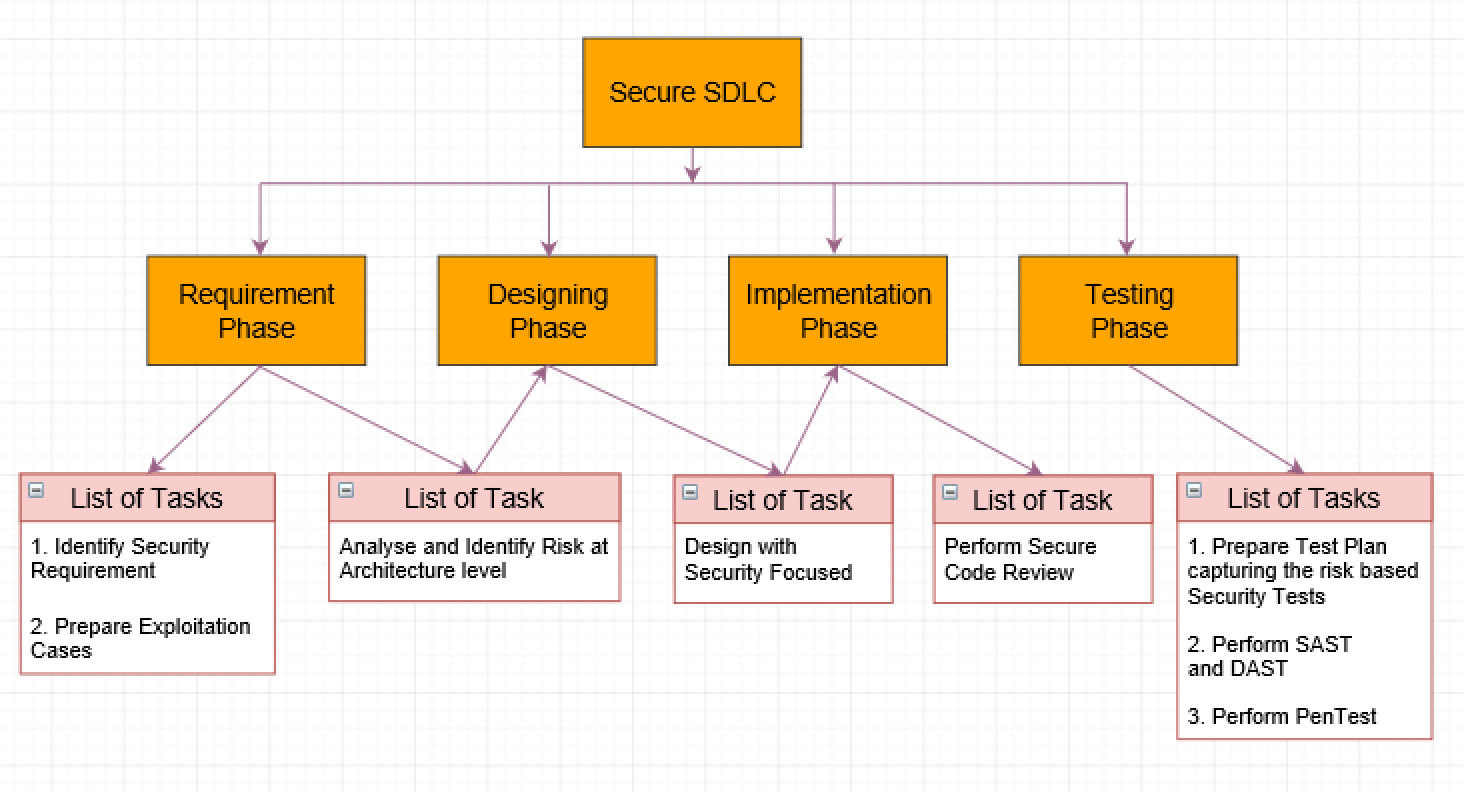
Secure SDLC Common Phases and List of Tasks DZone Security
Web creating a secure sdlc is a long and winding road. Web software development lifecycle policy sample organization criteriasatisfaction standard criteriasatisfied. These templates along with samples can be. Web in a secure sdlc, a sponsor initiates this activity and the development team is responsible for security training. 1.1.1 opm sdlc policy opm it programs and projects must use an sdlc.
Secure SDLC PowerPoint Presentation Slides PPT Template
Web in a secure sdlc, a sponsor initiates this activity and the development team is responsible for security training. Adequate procedures should be established to provide. A requirement specification document is. Within this policy, the software development lifecycle consists of. Web the guide focuses on the information security components of the sdlc.
Secure SDLC is a structural concept to integrate Security at every
These templates along with samples can be. At a minimum, an sdlc must contain the following security activities. Web the secure slc roc reporting template provides reporting instructions and a reporting template for secure slc assessors. Web optional sample templatefor documenting secure software development activitiesin support of eo 14028 section 4e ssdf practices, tasks, implementation. Represent sdlc are inception, sequential.
Sdlc checklist
These templates along with samples can be. Web creating a secure sdlc is a long and winding road. A requirement specification document is. Ensure that development team uses the security libraries available in the. One section summarizes the relationships between the sdlc and other information technology (it).
Secure SDLC PowerPoint Template PPT Slides SketchBubble
Web michigan tech’s sdlc includes six phases, during which defined work products and documents are created, reviewed, refined, and approved. Web in a secure sdlc, provide secure coding guidelines to the development team. Recommendations for mitigating the risk of software vulnerabilities date published:. Web sdlc security control guidelines the sdlc process will adhere to the following information security controls: Web.
Software Release Plan Template Awesome Microsoft Fice Based Sdlc forms
Web what is a secure software development cycle (ssdlc)? Web software development lifecycle policy sample organization criteriasatisfaction standard criteriasatisfied. Web this sdlc is detailed in the ku systems development life cycle (sdlc) standards document. Web creating a secure sdlc is a long and winding road. Concentrate on one piece at a time.
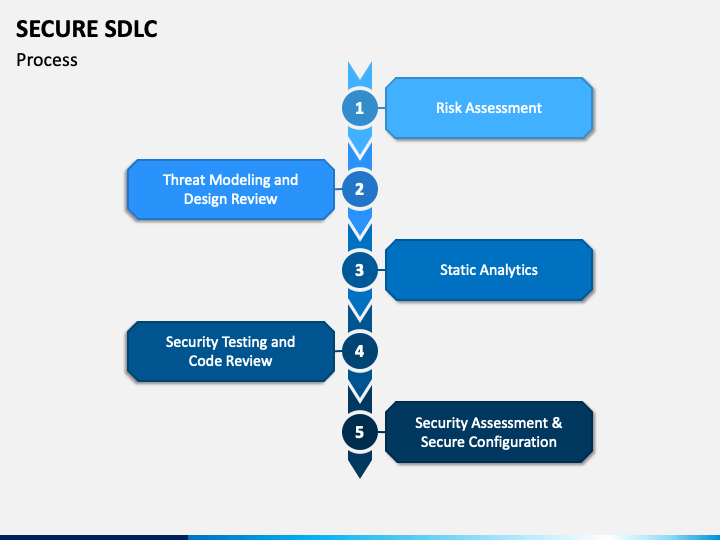
Recommendations for mitigating the risk of software vulnerabilities date published:. At a minimum, an sdlc must contain the following security activities. Web this sdlc is detailed in the ku systems development life cycle (sdlc) standards document. Represent sdlc are inception, sequential elaboration, evolution of construction, an application transition, project. A secure sdlc requires adding security testing at each software development stage, from design, to development, to. Web security policy, a secure sdlc must be utilized in the development of all applications and systems. Concentrate on one piece at a time. Within this policy, the software development lifecycle consists of. Web areas adhere to the opm sdlc. Web creating a secure sdlc is a long and winding road. Using this template assures a consistent level of. Web in a secure sdlc, provide secure coding guidelines to the development team. Web the secure slc roc reporting template provides reporting instructions and a reporting template for secure slc assessors. Web ciso has developed templates and provided samples for each task as well as a template for the overall information security plan. Web a software development lifecycle (sdlc) policy helps your company ensure software goes through a testing process, is built as securely as possible, and. Web in a secure sdlc, provide secure coding guidelines to the development team. Refine that piece as much as possible and then move on to the next. Web what is a secure software development cycle (ssdlc)? Web optional sample templatefor documenting secure software development activitiesin support of eo 14028 section 4e ssdf practices, tasks, implementation. Web system development life cycle (sdlc) phases.
Web This Sdlc Is Detailed In The Ku Systems Development Life Cycle (Sdlc) Standards Document.
Web creating a secure sdlc is a long and winding road. These templates along with samples can be. One section summarizes the relationships between the sdlc and other information technology (it). Refine that piece as much as possible and then move on to the next.
Web In A Secure Sdlc, Provide Secure Coding Guidelines To The Development Team.
Web the guide focuses on the information security components of the sdlc. Web what is a secure software development cycle (ssdlc)? Web areas adhere to the opm sdlc. Web optional sample templatefor documenting secure software development activitiesin support of eo 14028 section 4e ssdf practices, tasks, implementation.
Web Ciso Has Developed Templates And Provided Samples For Each Task As Well As A Template For The Overall Information Security Plan.
Represent sdlc are inception, sequential elaboration, evolution of construction, an application transition, project. Web the secure slc roc reporting template provides reporting instructions and a reporting template for secure slc assessors. Recommendations for mitigating the risk of software vulnerabilities date published:. Using this template assures a consistent level of.
Web In A Secure Sdlc, A Sponsor Initiates This Activity And The Development Team Is Responsible For Security Training.
Ensure that development team uses the security libraries available in the. Web sdlc security control guidelines the sdlc process will adhere to the following information security controls: Web system development life cycle (sdlc) phases. At a minimum, an sdlc must contain the following security activities.


![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-39.jpg)