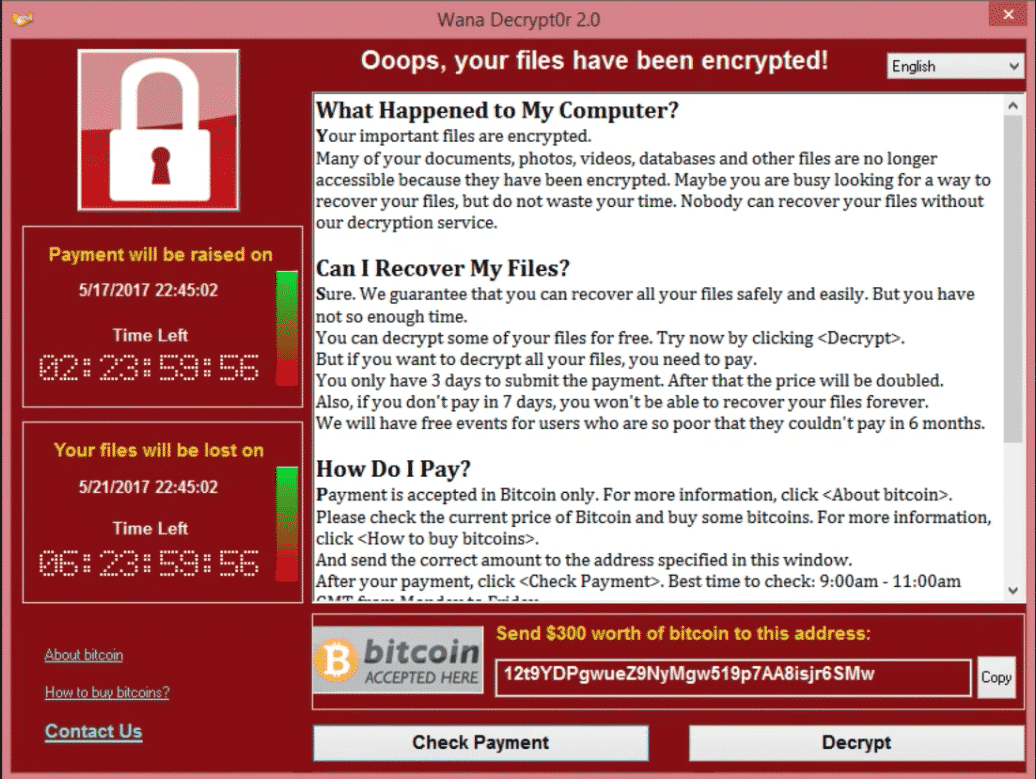
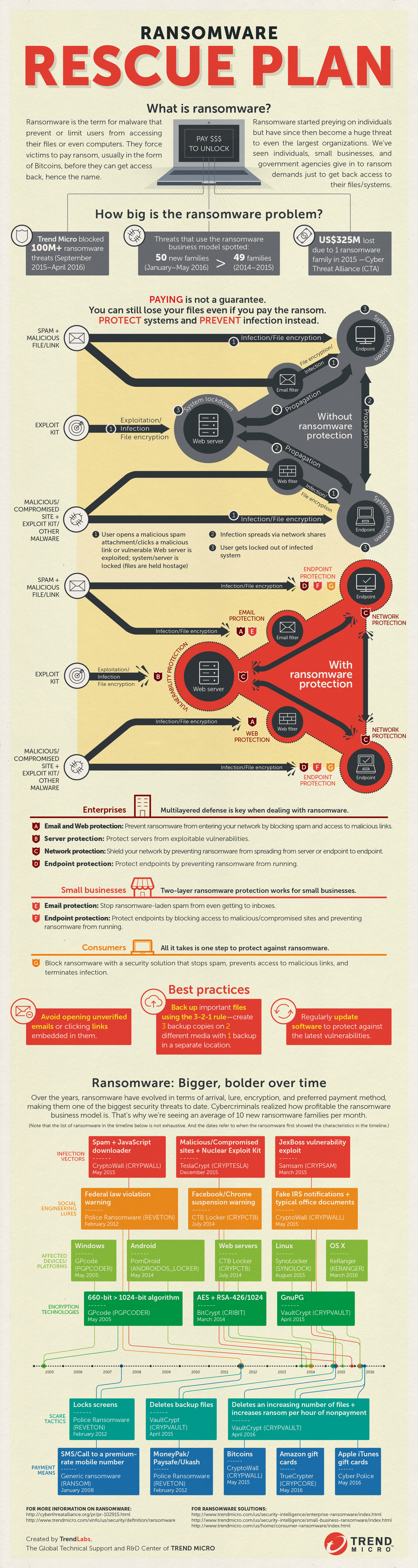
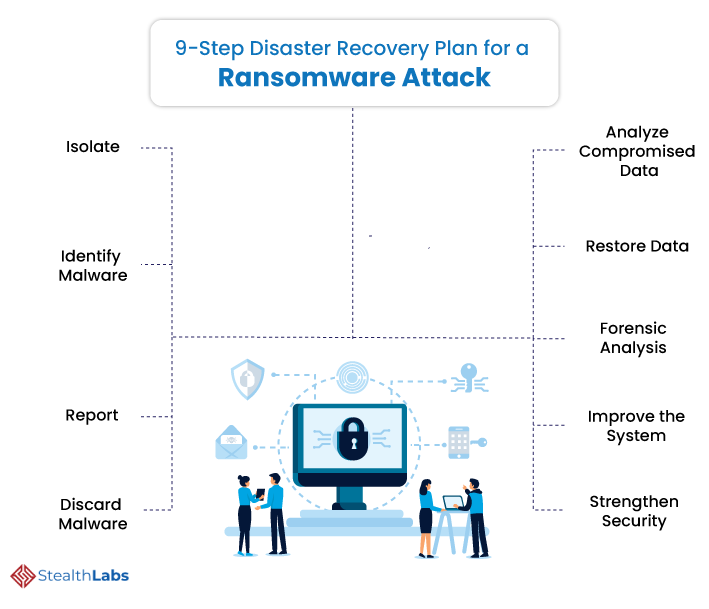
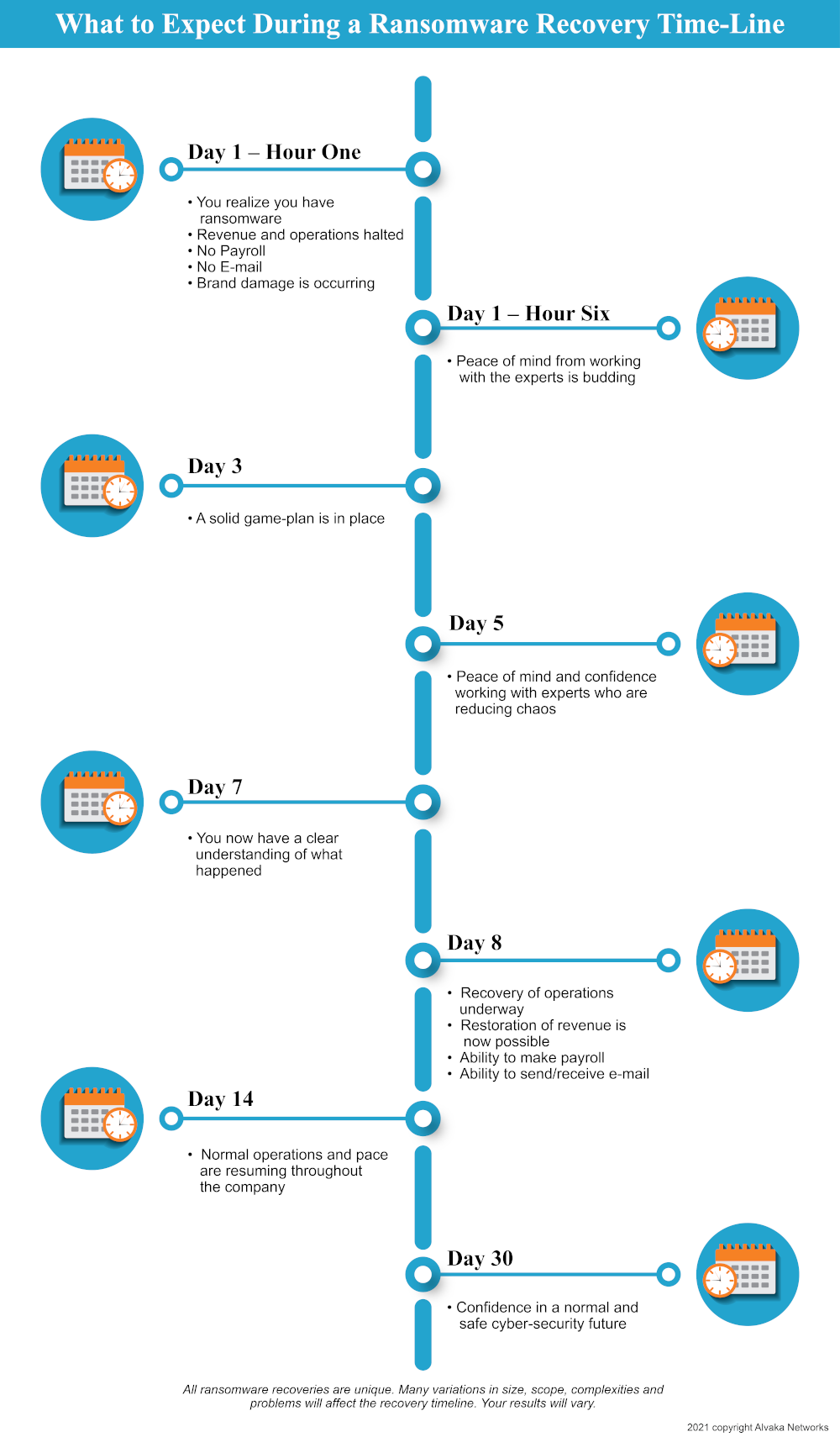
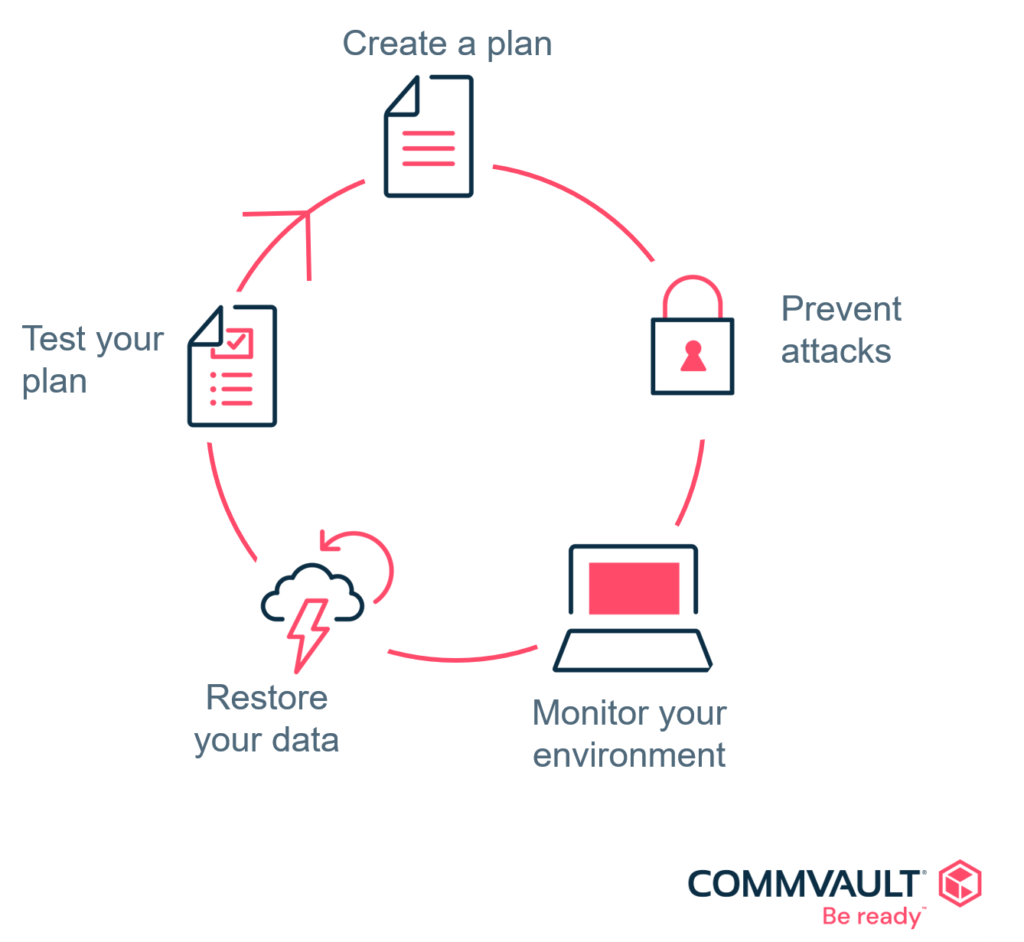
Ransomware Recovery Plan Template
Ransomware Recovery Plan Template - All hands on deck are needed after a ransomware attack. Tags disaster recovery, security incident response, backup strategy, crisis management, resilience. Web use the template to design and socialize your ransomware response plans. Ad eliminate the ransomware protection security gap. Your ransomware incident response plan should be written with input from all of the relevant stakeholders, including your cyber and it teams and. Ad we work with all major insurance companies. Discover the missing link in today's ransomware protection stack Web read key planning steps, and download a free template to get started. This section should provide an overview of the project and the purpose of. Web bulk vm processing operates within the existing guided ransomware recovery workflow, which spans across identification, validation and restore of recovery.
Disaster Recovery Plan Development is a MUST Eagle Consulting
Web read key planning steps, and download a free template to get started. Learn how to prevent losing your data from a ransomware attack with veeam. Web use the template to design and socialize your ransomware response plans. Continue with phase 2 to limit the scope of damage of an attack by protecting privileged roles. This section should provide an.
Simple Disaster Recovery Plan Template Luxury Simple Information
Web ransomware incident response plan template define the scope of the attack disable affected systems assess the damage disclose the attack prepare a. Web “every 11 seconds” a new organization will fall victim to ransomware, according to market researcher cybersecurity ventures.1 ransomware playbook to pay or not to pay?. Web fortunately, organizations can take steps to prepare for ransomware attacks..
Preventing Ransomware What Your Business Needs To Know
Web 3 introduction 3 types of ransomware attacks 3 encryption ransomware 4 nas ransomware 4 lock screen ransomware 4 hardware locker 4 application / web. Discover the missing link in today's ransomware protection stack Ad get the ransomware kit with the proprietary white paper, deep dive webinar, and free trial. Ad eliminate the ransomware protection security gap. Web also, paying.
Ransomware Rescue Plan Insight
Ad reduce your risk of data loss and downtime and protect data across multisite deployments. Web fortunately, organizations can take steps to prepare for ransomware attacks. This includes protecting data and devices from ransomware and being ready to respond. Learn how hpe greenlake for disaster recovery enables fast recovery from any disruption. Web also, paying proves ransomware works and could.
Ransomware Threat All You Need To Know!
Continue with phase 2 to limit the scope of damage of an attack by protecting privileged roles. Ad get the ransomware kit with the proprietary white paper, deep dive webinar, and free trial. Ad eliminate the ransomware protection security gap. This includes protecting data and devices from ransomware and being ready to respond. Discover the missing link in today's ransomware.
Ransomware Prevention Resources Ransomware Rescue Consultancy
Ransomware prevention best practices be prepared refer to the best practices and references below to help manage the risk posed by ransomware and support your. Web “every 11 seconds” a new organization will fall victim to ransomware, according to market researcher cybersecurity ventures.1 ransomware playbook to pay or not to pay?. Web also, paying proves ransomware works and could increase.
3 stories about ransomware attacks that will blow your mind
Web a ransomware tabletop exercise is a powerful resource for disaster recovery planners. Web a dr plan is a living document that contains detailed instructions on how to respond to acts of nature, catastrophic errors, or—increasingly—cybercriminal attacks. By paul kirvan sharon shea, executive editor ransomware is a component in nearly 25% of all. Discover the missing link in today's ransomware.
A Closer Look at Ransomware Attacks Why They Still Work
Ad reduce your risk of data loss and downtime and protect data across multisite deployments. Web use the template to design and socialize your ransomware response plans. Find out how they work, then create one with our free template. Web read key planning steps, and download a free template to get started. Who is going to execute recovery?
9step ransomware incident response plan H11 Digital Forensics
Web 3 introduction 3 types of ransomware attacks 3 encryption ransomware 4 nas ransomware 4 lock screen ransomware 4 hardware locker 4 application / web. Ad get the ransomware kit with the proprietary white paper, deep dive webinar, and free trial. Continue with phase 2 to limit the scope of damage of an attack by protecting privileged roles. Ad we.
Data Center Disaster Recovery Plan Checklist Filetype Pdf
2) detection, identification, and analysis; Continue with phase 2 to limit the scope of damage of an attack by protecting privileged roles. Web bulk vm processing operates within the existing guided ransomware recovery workflow, which spans across identification, validation and restore of recovery. Web this rapid modernization plan (ramp) checklist helps you prepare your organization so that it has a.
Create detailed instructions microsoft has also found that many organizations struggle with the next level of the. Web a ransomware tabletop exercise is a powerful resource for disaster recovery planners. Web a dr plan is a living document that contains detailed instructions on how to respond to acts of nature, catastrophic errors, or—increasingly—cybercriminal attacks. This includes protecting data and devices from ransomware and being ready to respond. Web up to 20% cash back an incident response plan or playbook should cover all four stages of a breach: Ad get the ransomware kit with the proprietary white paper, deep dive webinar, and free trial. Find out how they work, then create one with our free template. All hands on deck are needed after a ransomware attack. 2) detection, identification, and analysis; Who is going to execute recovery? Continue with phase 2 to limit the scope of damage of an attack by protecting privileged roles. Web here are some of the sections that should be included in an rfp template: Web fortunately, organizations can take steps to prepare for ransomware attacks. Ad we work with all major insurance companies. Web read key planning steps, and download a free template to get started. By paul kirvan sharon shea, executive editor ransomware is a component in nearly 25% of all. Ad reduce your risk of data loss and downtime and protect data across multisite deployments. Employees are often busy dealing with impact assessments,. Ad backup your endpoints wherever they are with flexible solutions. Ad eliminate the ransomware protection security gap.
Who Is Going To Execute Recovery?
Web also, paying proves ransomware works and could increase attacks against you or other groups. Ad we work with all major insurance companies. This section should provide an overview of the project and the purpose of. Web a dr plan is a living document that contains detailed instructions on how to respond to acts of nature, catastrophic errors, or—increasingly—cybercriminal attacks.
Ransomware Prevention Best Practices Be Prepared Refer To The Best Practices And References Below To Help Manage The Risk Posed By Ransomware And Support Your.
Web read key planning steps, and download a free template to get started. Employees are often busy dealing with impact assessments,. Ad get the ransomware kit with the proprietary white paper, deep dive webinar, and free trial. Your ransomware incident response plan should be written with input from all of the relevant stakeholders, including your cyber and it teams and.
All Hands On Deck Are Needed After A Ransomware Attack.
By paul kirvan sharon shea, executive editor ransomware is a component in nearly 25% of all. Web 3 introduction 3 types of ransomware attacks 3 encryption ransomware 4 nas ransomware 4 lock screen ransomware 4 hardware locker 4 application / web. Continue with phase 2 to limit the scope of damage of an attack by protecting privileged roles. 2) detection, identification, and analysis;
Web A Ransomware Tabletop Exercise Is A Powerful Resource For Disaster Recovery Planners.
Ad backup your endpoints wherever they are with flexible solutions. Web bulk vm processing operates within the existing guided ransomware recovery workflow, which spans across identification, validation and restore of recovery. Web use the template to design and socialize your ransomware response plans. Tags disaster recovery, security incident response, backup strategy, crisis management, resilience.