Ransomware Policy Template
Ransomware Policy Template - Microsoft has discovered a new version of the blackcat ransomware that embeds the impacket networking framework and the remcom. Web if customer data is stolen, it may trigger state data breach notification laws. Malicious actors then demand ransom in exchange for decryption. Web so you may need a ransomware policy. To read about real examples of how companies and municipalities responded to a ransomware attack, please visit cyber readiness news. Ransomware prevention best practices be prepared refer to the best practices and references below to help manage the risk posed by ransomware and support your organization’s coordinated and efficient response to a ransomware incident. Read key planning steps, and download a free template to get started. Ransomware is a component in nearly 25% of all breaches, according to verizon's 2023 data breach investigations. Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. Web a ransomware incident response plan may be the difference between surviving an attack and shuttering operations.
A Closer Look at Ransomware Attacks Why They Still Work
Department of the treasury announced a set of actions designed to counter ransomware, principally by discouraging ransomware payments. Sign up for free at becyberready.com. Web on september 21, 2021, the u.s. Ransomware extortion and destructive attacks only work when all legitimate access to. Download our information and cyber security policy templates for smbs, startups, and enterprises.
Incident Response Services Security Risk LBMC
Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid. Quick and easy to customize. The estimated cost of restoration, the likelihood of successful restoration whether the ransom is paid or not, regulatory implications (see below), and the criticality of the data. Here are additional resources from nist and.
Overview of threat protection scenario Microsoft Docs
Ransomware actors often target and threaten to sell or leak exfiltrated data or authentication information if the ransom is not paid. Web new blackcat ransomware variant adopts advanced impacket and remcom tools. Microsoft on thursday disclosed that it found a new version of the blackcat ransomware (aka alphv and noberus) that embeds tools like impacket and remcom to facilitate lateral.
Preventing Ransomware What Your Business Needs To Know
This includes protecting data and devices from ransomware and being ready to respond to any ransomware attacks that succeed. Want to protect yourself from emerging. Web 21 hours agothe infamous blackcat ransomware group, also known as alphv, has claimed responsibility for an attack on watchmakers seiko, which happened earlier this month. You must have at least one app connected using.
Hybrid Ransomware Policy Commercial Crime Concepts
I have developed a new sample ransomware prevention policy and response procedure that is available on the premium members section of our veterans press website at www.veteranspress.com. Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. Web on september 21, 2021, the u.s..
Overview of threat protection scenario Microsoft Docs
This includes protecting data and devices from ransomware and being ready to respond to any ransomware attacks that succeed. Web get ahead of your 2023 security goals. Download our information and cyber security policy templates for smbs, startups, and enterprises. Malicious actors then demand ransom in exchange for decryption. Nuspire's q2 2023 cyber threat report shows rapid growth of cl0p.
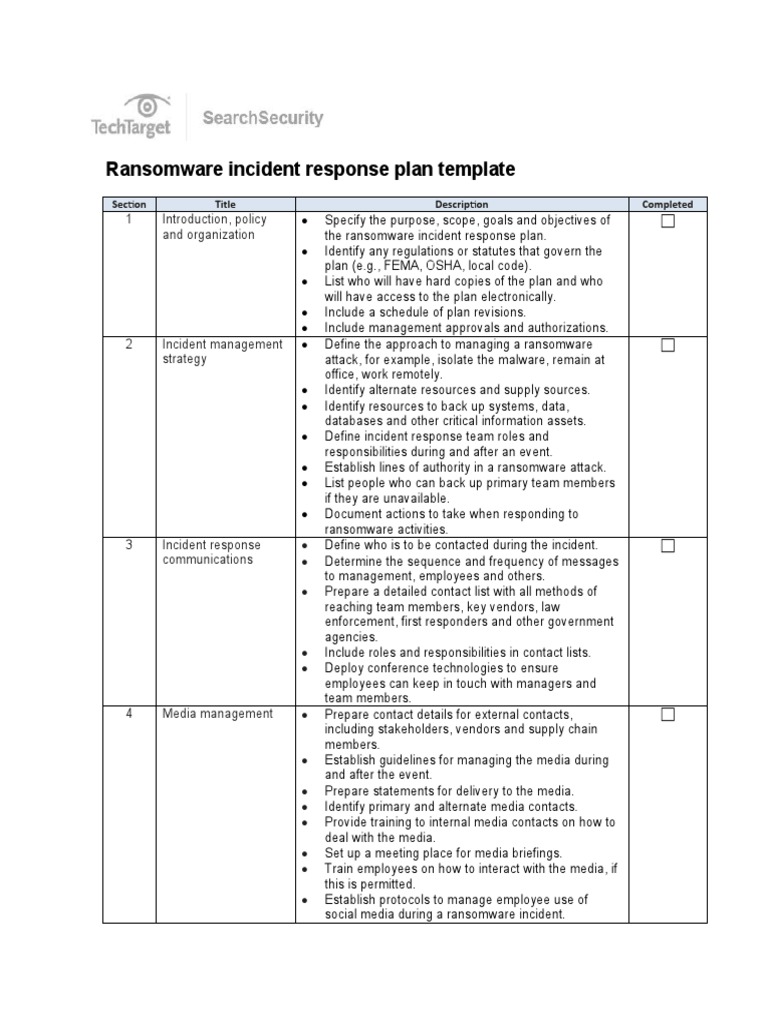
Ransomware Incident Response Plan Template PDF Ransomware
Web some ransomware variants only affect certain tools (e.g., databases) or platforms (e.g., <a. To read about real examples of how companies and municipalities responded to a ransomware attack, please visit cyber readiness news. The estimated cost of restoration, the likelihood of successful restoration whether the ransom is paid or not, regulatory implications (see below), and the criticality of the.
Ransomware Prevention Guide
Web 21 hours agoransomware takes center stage in q2 2023. Unique slides with a clean and professional look. The playbook defines key stakeholders, processes, policies & prevention plans to defend your organization. To read about real examples of how companies and municipalities responded to a ransomware attack, please visit cyber readiness news. Web so you may need a ransomware policy.
Ransomware Negotiation Tips LMG Security
Nuspire's q2 2023 cyber threat report shows rapid growth of cl0p ransomware gang. Web ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. It’s listed as ransomware policy with a little new sign after it. This includes protecting data and devices from ransomware and being.
Defending Against Ransomware Prevention, Protection, Removal
Here are nist resources that can help you with ransomware protection and response. Department of the treasury announced a set of actions designed to counter ransomware, principally by discouraging ransomware payments. Malicious actors then demand ransom in exchange for decryption. To read about real examples of how companies and municipalities responded to a ransomware attack, please visit cyber readiness news..
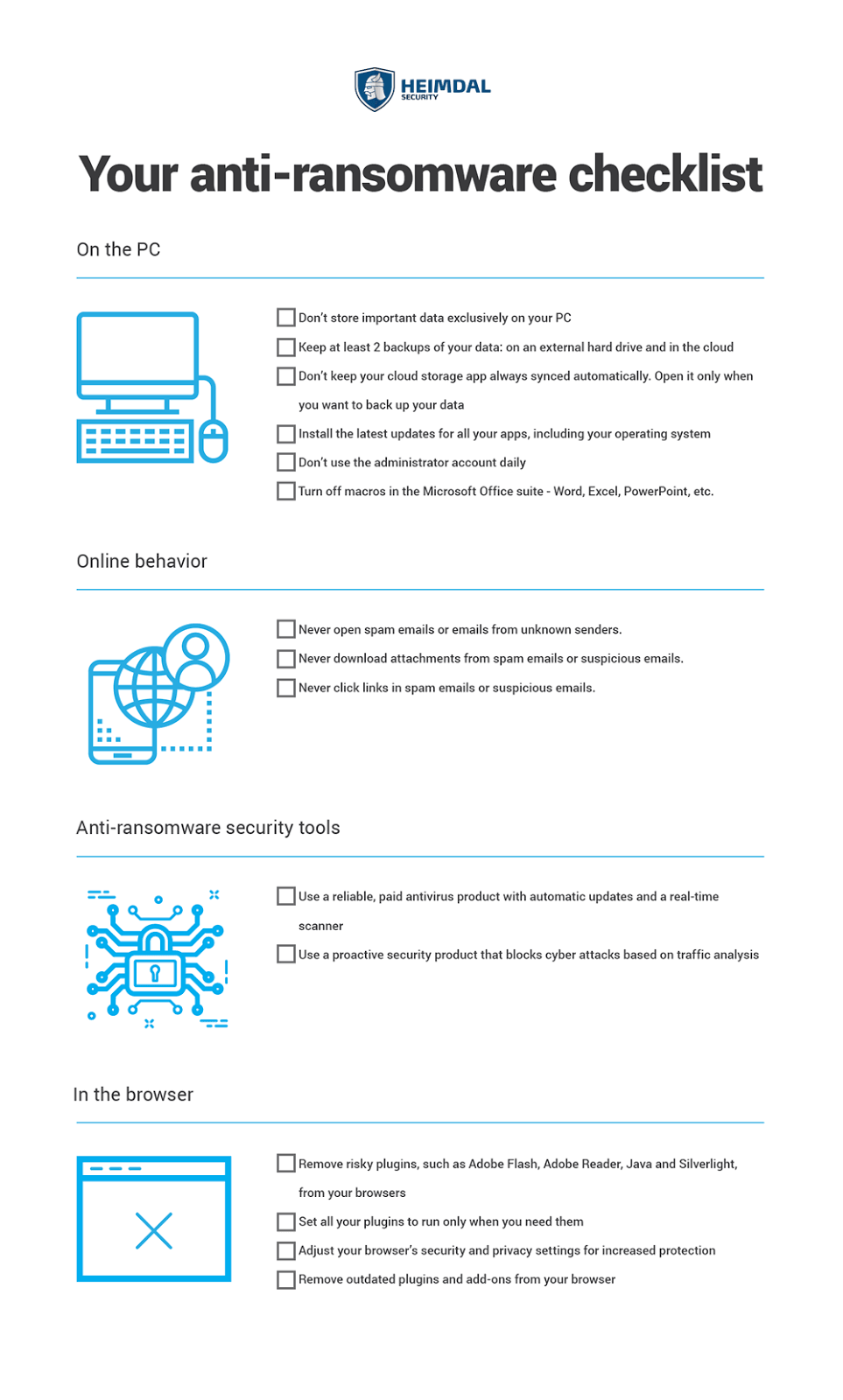
Web you must implement data protection to ensure rapid and reliable recovery from a ransomware attack and to block some techniques of attackers. Sign up for free at becyberready.com. The estimated cost of restoration, the likelihood of successful restoration whether the ransom is paid or not, regulatory implications (see below), and the criticality of the data. The malicious cyber actor holds systems or data hostage until the ransom is paid. Ransomware prevention best practices be prepared refer to the best practices and references below to help manage the risk posed by ransomware and support your organization’s coordinated and efficient response to a ransomware incident. Here are nist resources that can help you with ransomware protection and response. Blackcat's sphynx ransomware embeds impacket, remcom. Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. Unique slides with a clean and professional look. Web fortunately, organizations can take steps to prepare for ransomware attacks. Nuspire's q2 2023 cyber threat report shows rapid growth of cl0p ransomware gang. Microsoft has discovered a new version of the blackcat ransomware that embeds the impacket networking framework and the remcom. Web create the policy. Malicious actors then demand ransom in exchange for decryption. Here are additional resources from nist and partner federal agencies to help you protect against and respond to ransomware attacks : Web part 1 provides guidance for all organizations to reduce the impact and likelihood of ransomware incidents and data extortion, including best practices to prepare for, prevent, and mitigate these incidents. Web new blackcat ransomware variant adopts advanced impacket and remcom tools. Automatic detection of potential ransomware activity. Preparing your organization for ransomware attacks. Web a ransomware incident response plan may be the difference between surviving an attack and shuttering operations.
Web On September 21, 2021, The U.s.
Blackcat's sphynx ransomware embeds impacket, remcom. Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. Want to protect yourself from emerging. Web risk management implement security measures sufficient to reduce identified threats and vulnerabilities to a reasonable and appropriate level access controls ensure access rights granted are not excessive business associate agreements define processes, including responsibilities, to prevent, manage and report security incidents and breaches
Ransomware Actors Often Target And Threaten To Sell Or Leak Exfiltrated Data Or Authentication Information If The Ransom Is Not Paid.
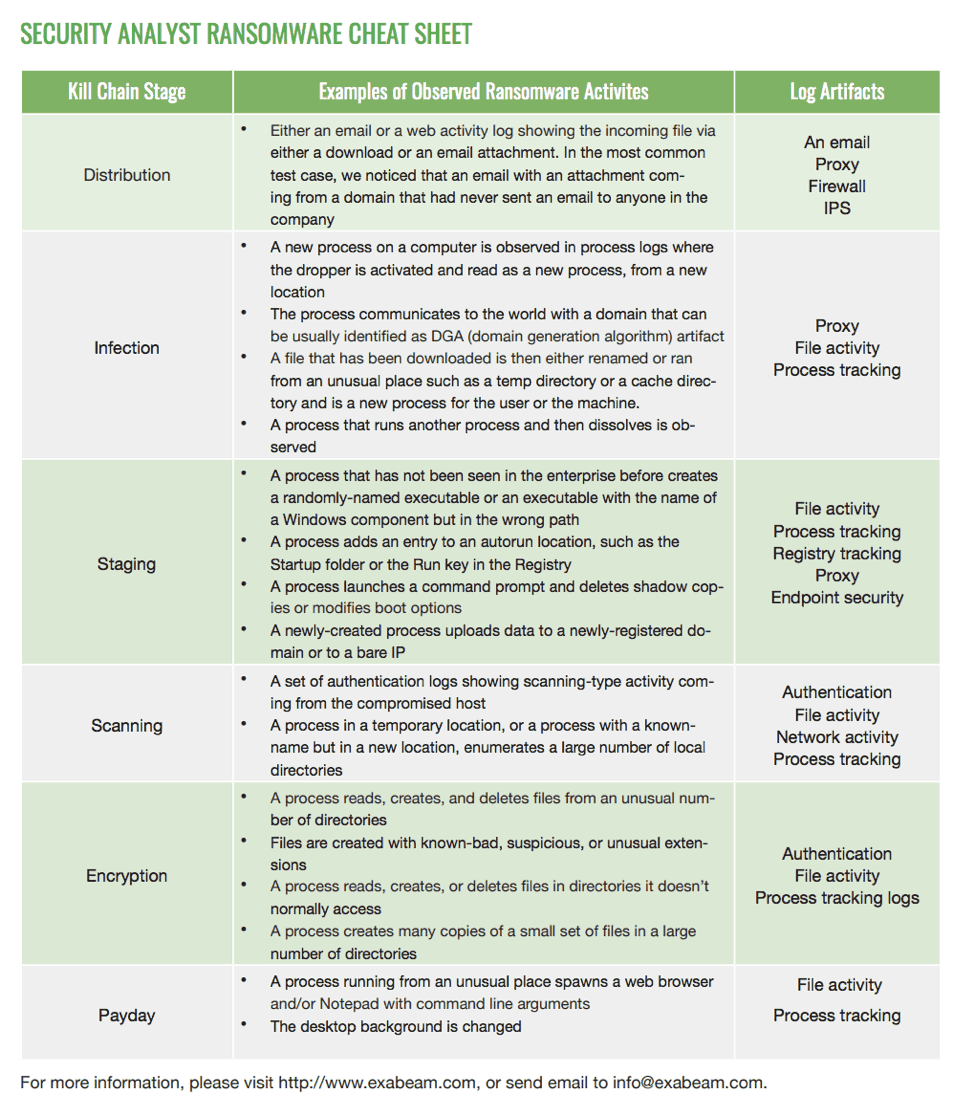
Unique slides with a clean and professional look. The workflow is aimed at team leaders who need to coordinate actions through each stage of incident response, from detection to recovery. Web part 1 provides guidance for all organizations to reduce the impact and likelihood of ransomware incidents and data extortion, including best practices to prepare for, prevent, and mitigate these incidents. After the initial infection, the ransomware attempts to spread to shared storage drives and other accessible systems.
Nuspire's Q2 2023 Cyber Threat Report Shows Rapid Growth Of Cl0P Ransomware Gang.
Web some ransomware variants only affect certain tools (e.g., databases) or platforms (e.g., <a. Web so you may need a ransomware policy. Ransomware extortion and destructive attacks only work when all legitimate access to. The estimated cost of restoration, the likelihood of successful restoration whether the ransom is paid or not, regulatory implications (see below), and the criticality of the data.
Here Are Nist Resources That Can Help You With Ransomware Protection And Response.
Download our information and cyber security policy templates for smbs, startups, and enterprises. Microsoft on thursday disclosed that it found a new version of the blackcat ransomware (aka alphv and noberus) that embeds tools like impacket and remcom to facilitate lateral movement and remote code execution. Web ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Automatic detection of potential ransomware activity.