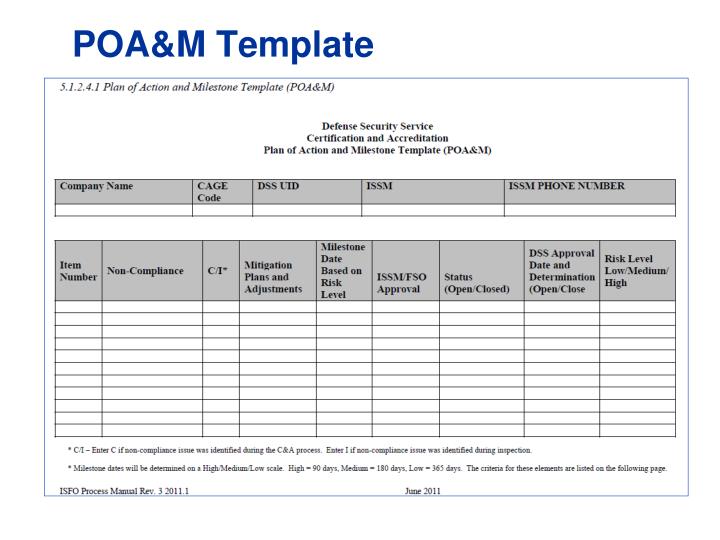
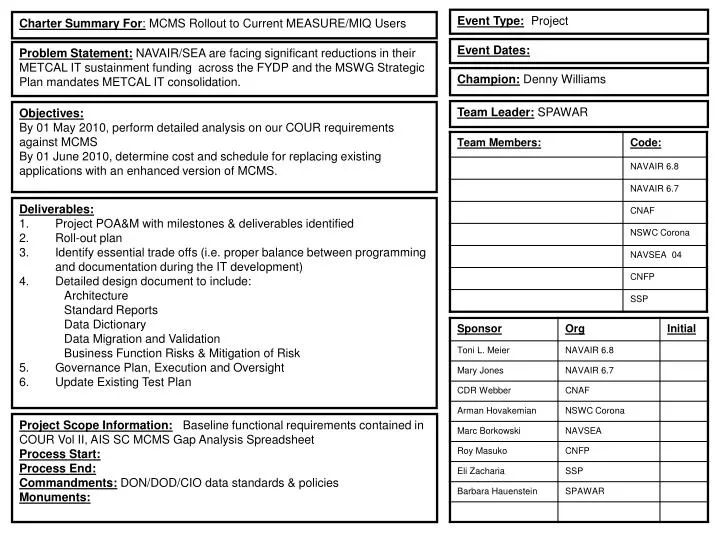
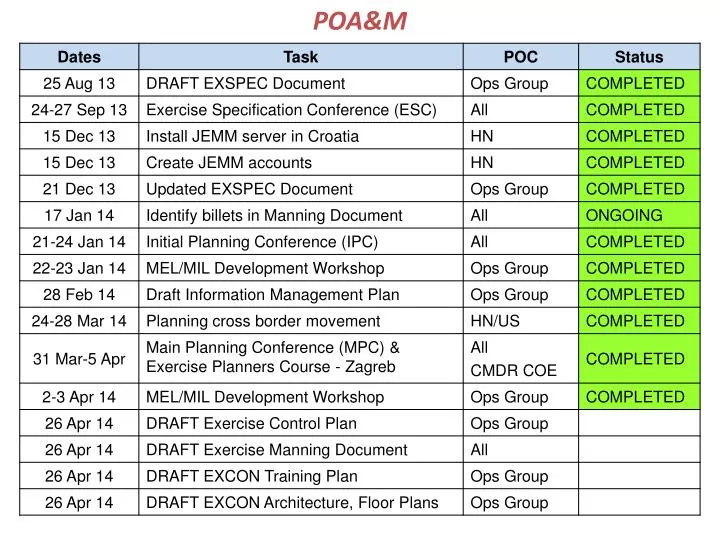
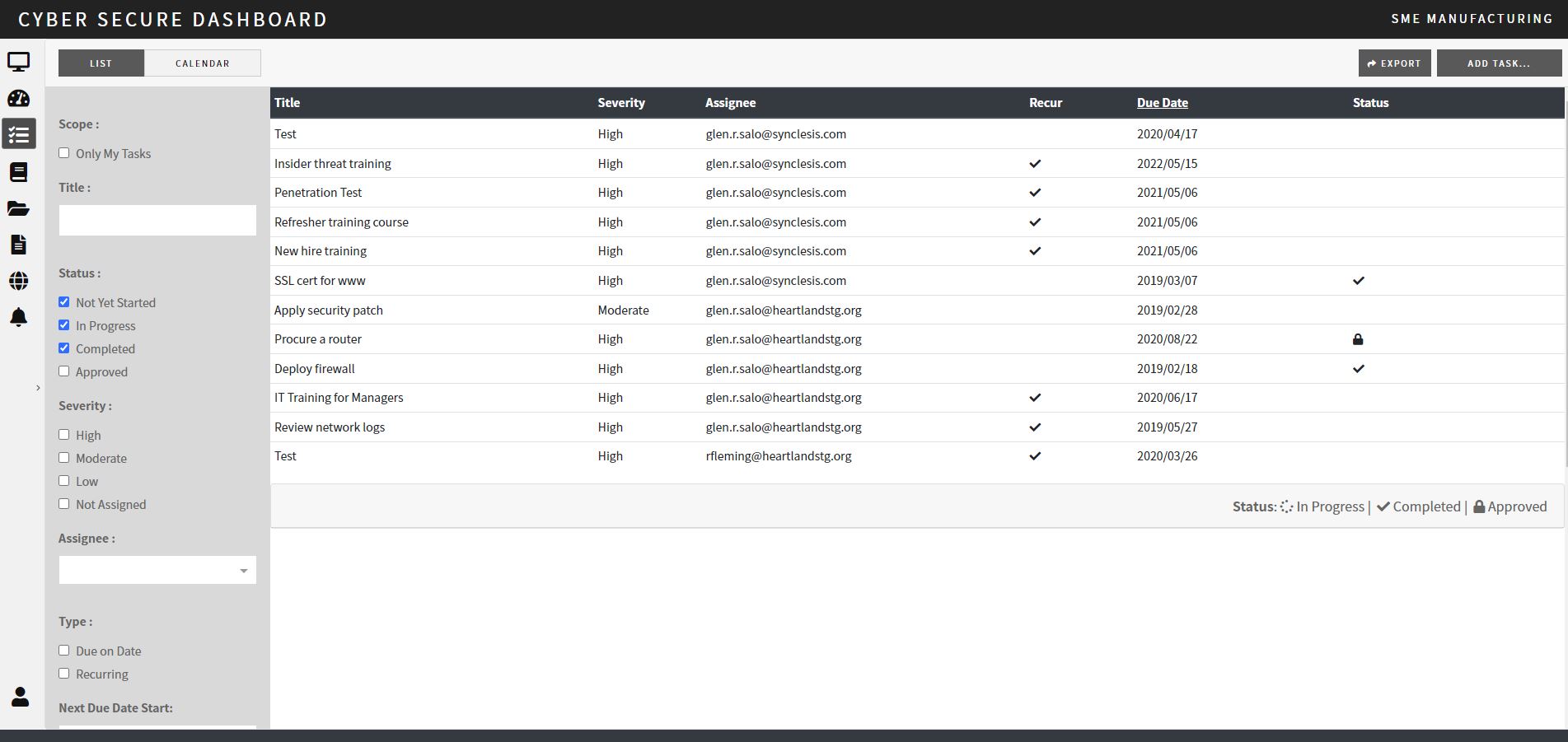
Poa&M Template Excel
Poa&M Template Excel - Web date poa&m item was last changed or closed identifier specified in the inventory this is a unique string associated with the asset, it could just be ip, or any arbitrary naming scheme. Completion dates shall be determined based on a realistic estimate of the amount of time it will take to procure/allocate the resources required for the corrective. All applicable cells in the poa&m template for findings/ weaknesses must be completed. Be sure to include the total funding requirements in the security costs field in column 13 of the poa&m. Free shipping on qualified orders. Web poa&m template user guide, v1.0february 18, 2015. Web system level and program level findings/weaknesses must be documented and divided into two (2) separate templates. Web using automation to create a poa&m. If during your internal audit you find that your company does not meet some of the nist requirements,. Web dha privacy and civil liberties office:
NIST 800171 System Security Plan (SSP) & Plan of Action & Milestones
Web using automation to create a poa&m. Web dha privacy and civil liberties office: Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. The additional columns were added at the behest of agency partners to help them track cybersecurity and infrastructure security. Web a plan of action and milestones (poa&m) is a tool that.
PPT ODAA PowerPoint Presentation ID6519667
Free shipping on qualified orders. Web poa&m template user guide, v1.0february 18, 2015. You want to identify what control is associated with it so that you. Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf. A poa&m is a corrective action plan for tracking.
Beautiful Work Making A Timeline In Excel Poa&m Template Example Of
The additional columns were added at the behest of agency partners to help them track cybersecurity and infrastructure security. Web june 28 | 2022. Plan of action and milestones template. You want to keep track of all your poa&m objectives by identifying them by a unique number or identifier. You want to identify what control is associated with it so.
PPT Deliverables Project POA&M with milestones & deliverables
Recommended when significant mitigation steps are warranted. Using the applications available from lake ridge you can auto generate your plan of action & milestones document. It details the resources (e.g., personnel,. Free, easy returns on millions of items. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses.
Smart Action Plan Template Excel Inspirational Poa&m format
Ad enjoy low prices on earth's biggest selection of books, electronics, home, apparel & more. Free, easy returns on millions of items. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. You want to keep track of all your poa&m objectives by identifying them by a unique number or identifier..
PPT POA&M PowerPoint Presentation, free download ID3204262
Completion dates shall be determined based on a realistic estimate of the amount of time it will take to procure/allocate the resources required for the corrective. All applicable cells in the poa&m template for findings/ weaknesses must be completed. Web system level it security poa&m example enclave is type: Web the fedramp poam template (.xlsm). Free shipping on qualified orders.
Plan of Action and Milestones (POA&M) CYBER SECURE DASHBOARD
Web date poa&m item was last changed or closed identifier specified in the inventory this is a unique string associated with the asset, it could just be ip, or any arbitrary naming scheme. Web the first thing you need to do is identify a poa&m id numbering system. Completion dates shall be determined based on a realistic estimate of the.
Security assessment Plan Template Fresh Nist 800 171 Poa&m Template
A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. Web june 28 | 2022. Web system level it security poa&m example enclave is type: Think of it as the ultimate to do list on your path to information technology security and. Web using this job aid this job aid is.
Nist 800171 Poam Template
You want to identify what control is associated with it so that you. Web the first thing you need to do is identify a poa&m id numbering system. Web using automation to create a poa&m. Web the project plan in ms excel format, sometimes called a plan of actions and milestones (poam), uses a method of planning called raci that.
Poa&M Template Dod Flyer Template
Web using automation to create a poa&m. Lake ridge apps, allow you to manage your poa&m items by managing due dates, staff, and budgets. A poa&m is a corrective action plan for tracking and planning the resolution of information security and privacy weaknesses. The additional columns were added at the behest of agency partners to help them track cybersecurity and.
Free, easy returns on millions of items. Ad enjoy low prices on earth's biggest selection of books, electronics, home, apparel & more. If during your internal audit you find that your company does not meet some of the nist requirements,. The additional columns were added at the behest of agency partners to help them track cybersecurity and infrastructure security. Free shipping on qualified orders. Web a plan of action and milestones (poa&m) is a tool that allows you to list strategically your vulnerabilities and the countermeasures you must take to eliminate them. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf. Web implementation of an effective plan of action and milestones (poa&m) strategy. Web system level and program level findings/weaknesses must be documented and divided into two (2) separate templates. Lake ridge apps, allow you to manage your poa&m items by managing due dates, staff, and budgets. Completion dates shall be determined based on a realistic estimate of the amount of time it will take to procure/allocate the resources required for the corrective. You want to identify what control is associated with it so that you. Plan of action and milestones template. Think of it as the ultimate to do list on your path to information technology security and. Web using automation to create a poa&m. Web dha privacy and civil liberties office: Fedramp plan of action and milestones (poa&m) template completion guide last modified by: Web date poa&m item was last changed or closed identifier specified in the inventory this is a unique string associated with the asset, it could just be ip, or any arbitrary naming scheme. You want to keep track of all your poa&m objectives by identifying them by a unique number or identifier.
A Poa&M Is A Corrective Action Plan For Tracking And Planning The Resolution Of Information Security And Privacy Weaknesses.
Overview of poa&m this section provides a general overview of the poa&m: Lake ridge apps, allow you to manage your poa&m items by managing due dates, staff, and budgets. Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf. The additional columns were added at the behest of agency partners to help them track cybersecurity and infrastructure security.
You Want To Identify What Control Is Associated With It So That You.
Free shipping on qualified orders. Plan of action and milestones template. Web system level it security poa&m example enclave is type: Recommended when significant mitigation steps are warranted.
Using The Applications Available From Lake Ridge You Can Auto Generate Your Plan Of Action & Milestones Document.
All findings/weaknesses must be associated with at. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. Web dha privacy and civil liberties office: If during your internal audit you find that your company does not meet some of the nist requirements,.
It Details The Resources (E.g., Personnel,.
Web june 28 | 2022. Web the first thing you need to do is identify a poa&m id numbering system. Web using automation to create a poa&m. Be sure to include the total funding requirements in the security costs field in column 13 of the poa&m.