Insider Threat Policy Template
Insider Threat Policy Template - Web an insider threat is when a current or former employee, contractor or business partner, who has or had authorized access to an organization’s network systems, data or premises,. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Establishes policy and assigns responsibilities within dod to develop and maintain an insider threat program to comply with the requirements and minimum. Web to help understand the gravity of the insider threat factor, let’s look at some examples. Web the new definitions of “insider threat” and “insider” expands upon the definitions found in eo 13587 and the national insider threat policy and minimum standards for executive. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. An insider threat is a type of cyberattack originating from an individual who works for an organization or has authorized access to its networks or. Web information to establish insider threat detection and prevention programs. This plan establishes policy and assigns responsibilities for the insider threat program (itp). Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field.
Security Insider Threat Safety Central
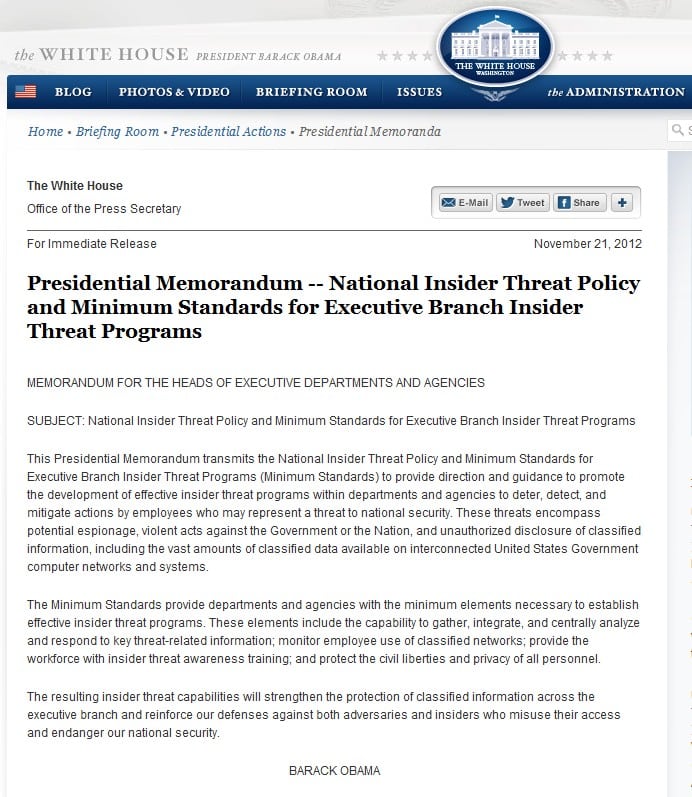
An insider threat is a type of cyberattack originating from an individual who works for an organization or has authorized access to its networks or. In november 2012, the president issued the national insider threat policy and the minimum. Insider threat indicators in uam june 2023, 7. This plan establishes policy and assigns responsibilities for the insider threat program (itp)..
Building an Insider Threat Management Program Divurgent
On cisa.gov, visitors will find. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web to help understand the gravity of the insider threat factor, let’s look at some examples. Web an insider threat is when a current or former employee, contractor or business partner, who has or had authorized access.
How to Prevent Insider Threats Case Studies, Examples, Types (2022)
In november 2012, the president issued the national insider threat policy and the minimum. The itp will establish a secure operating environment for. Web the national insider threat policy aims to strengthen the protection and safeguarding of classified information by: On cisa.gov, visitors will find. Web 10 steps to create an efficient insider threat program.
Breaking White House Announces “Insider Threat” Policy Archives
Web an insider threat is when a current or former employee, contractor or business partner, who has or had authorized access to an organization’s network systems, data or premises,. This plan establishes policy and assigns responsibilities for the insider threat program (itp). Web the insider threat mission is a dynamic effort requiring constant evaluation, fresh perspectives, and updated approaches. Web.
Protecting against insider risks in an uncertain environment
Insider threat indicators in uam june 2023, 7. An insider threat is a type of cyberattack originating from an individual who works for an organization or has authorized access to its networks or. Web insider threat roadmap 2020 administrator’s message am proud to present the transportation security administration’s (tsa) insider threat roadmap. Web this toolkit will quickly point you to.
Cybersecurity HQ An Insider Attack on the Industry
More industry insider threat information and resources. In november 2012, the president issued the national insider threat policy and the minimum. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. Web information to establish insider threat detection and prevention programs. This plan establishes policy and assigns.
Insider Threat Program Template Template Resume Examples QBD3E4RYOX
Web national insider threat policy the national insider threat policy aims to strengthen the protection and safeguarding of classified information by: Examples of an insider may. On cisa.gov, visitors will find. More industry insider threat information and resources. Web cisa defines insider threat as the threat that an insider will use their authorized access, wittingly or unwittingly, to do harm.
Insider Threat Plan Template Master of Documents
Web insider threat roadmap 2020 administrator’s message am proud to present the transportation security administration’s (tsa) insider threat roadmap. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field..
Insider Threat Mitigation
Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; Web insider threat roadmap 2020 administrator’s message am proud to present the transportation security administration’s (tsa) insider threat roadmap. Web a current or former employee, contractor, or business partner who has or had authorized access to the organization’s network, systems, or data..
Insider Threat Report SC Report Template Tenable®
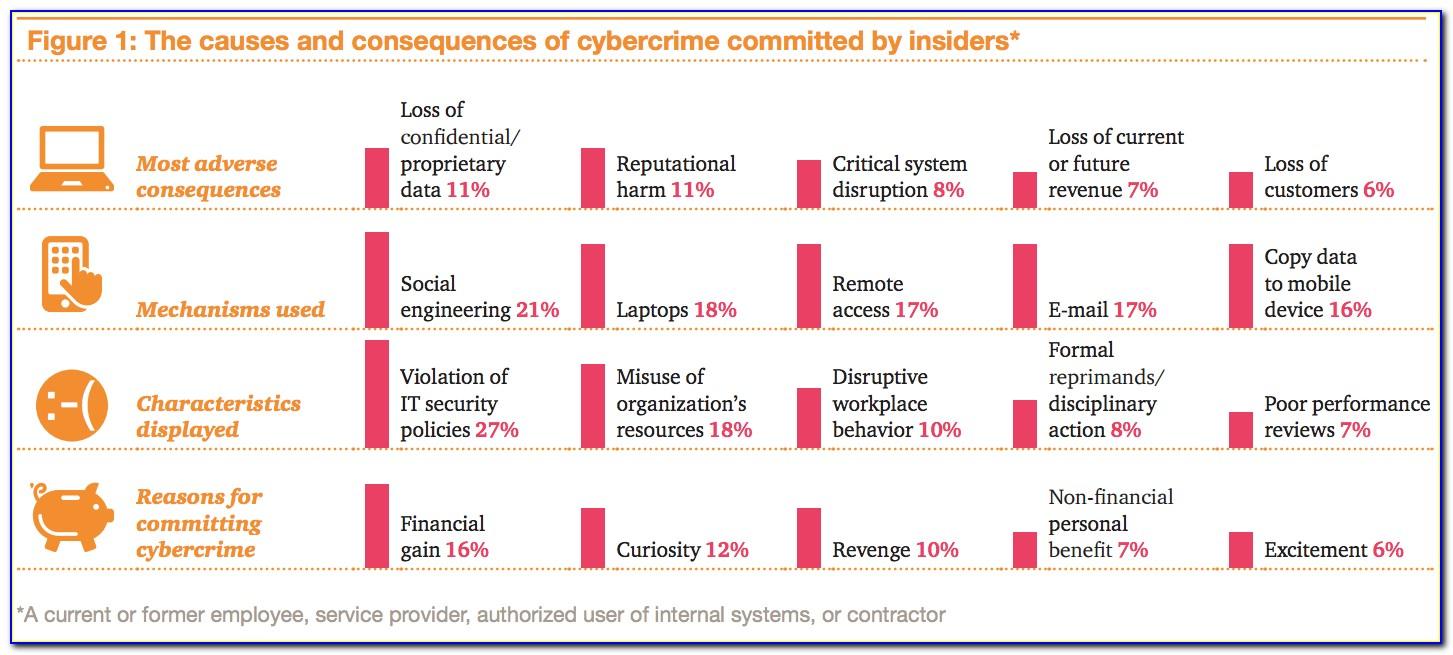
Attorneys steal and destroy data from their law firm. Web the new definitions of “insider threat” and “insider” expands upon the definitions found in eo 13587 and the national insider threat policy and minimum standards for executive. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; An insider threat is a.
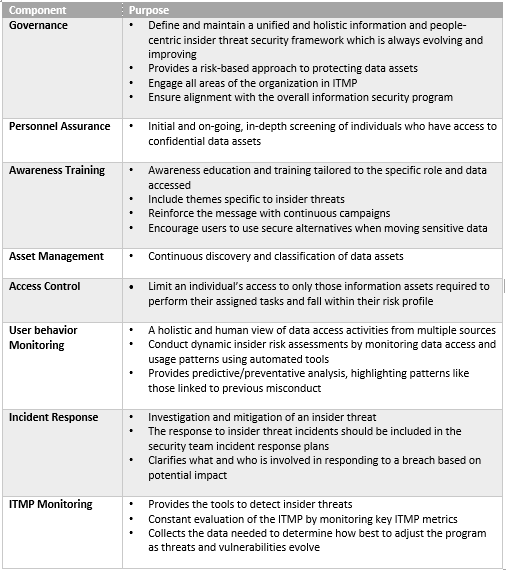
Web insider threat programs are designed to deter, detect, and mitigate actions by insiders who represent a threat to national security. Web information to establish insider threat detection and prevention programs. An insider threat is a type of cyberattack originating from an individual who works for an organization or has authorized access to its networks or. Web the national insider threat policy aims to strengthen the protection and safeguarding of classified information by: Web national insider threat policy the national insider threat policy aims to strengthen the protection and safeguarding of classified information by: Examples of an insider may. Defining the threat, detecting and identifying the threat, assessing the threat, and managing the threat. Web to help understand the gravity of the insider threat factor, let’s look at some examples. In november 2012, the president issued the national insider threat policy and the minimum. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field. More industry insider threat information and resources. Web a current or former employee, contractor, or business partner who has or had authorized access to the organization’s network, systems, or data. Insider threat indicators in uam june 2023, 7. Web 10 steps to create an efficient insider threat program. Establishes policy and assigns responsibilities within dod to develop and maintain an insider threat program to comply with the requirements and minimum. Attorneys steal and destroy data from their law firm. Web cisa defines insider threat as the threat that an insider will use their authorized access, wittingly or unwittingly, to do harm to the department’s mission, resources, personnel,. Web the insider threat mission is a dynamic effort requiring constant evaluation, fresh perspectives, and updated approaches. Web the new definitions of “insider threat” and “insider” expands upon the definitions found in eo 13587 and the national insider threat policy and minimum standards for executive. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments;
Web The New Definitions Of “Insider Threat” And “Insider” Expands Upon The Definitions Found In Eo 13587 And The National Insider Threat Policy And Minimum Standards For Executive.
On cisa.gov, visitors will find. An insider threat is a type of cyberattack originating from an individual who works for an organization or has authorized access to its networks or. Web information to establish insider threat detection and prevention programs. Web this toolkit will quickly point you to the resources you need to help you perform your role in the insider threat field.
The Itp Will Establish A Secure Operating Environment For.
Web the national insider threat policy aims to strengthen the protection and safeguarding of classified information by: Web an insider threat is when a current or former employee, contractor or business partner, who has or had authorized access to an organization’s network systems, data or premises,. Insider threat indicators in uam june 2023, 7. Web insider threat roadmap 2020 administrator’s message am proud to present the transportation security administration’s (tsa) insider threat roadmap.
Web National Insider Threat Policy The National Insider Threat Policy Aims To Strengthen The Protection And Safeguarding Of Classified Information By:
Establishes policy and assigns responsibilities within dod to develop and maintain an insider threat program to comply with the requirements and minimum. In november 2012, the president issued the national insider threat policy and the minimum. Web the insider threat mitigation guide provides comprehensive information to help federal, state, local, tribal, and territorial governments; More industry insider threat information and resources.
Examples Of An Insider May.
Web 10 steps to create an efficient insider threat program. Web to help understand the gravity of the insider threat factor, let’s look at some examples. Attorneys steal and destroy data from their law firm. This plan establishes policy and assigns responsibilities for the insider threat program (itp).