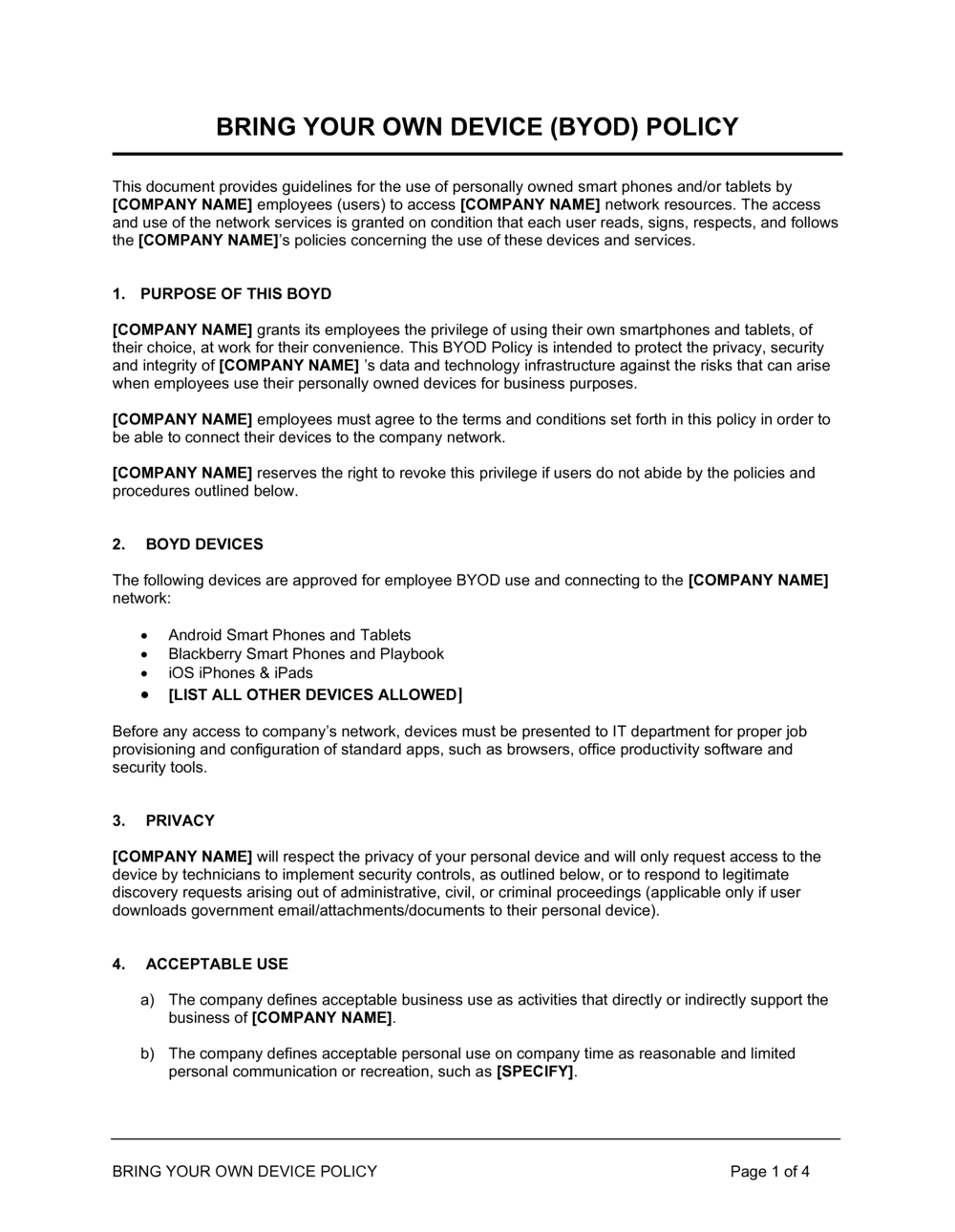
Acceptable Use Policy Template Nist
Acceptable Use Policy Template Nist - These are free to use and fully customizable to your company's it security practices. Teleworkers should ensure that all the devices on their wired and wireless home. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Web the draft update, which nist has released for public comment, reflects changes in the cybersecurity landscape and makes it easier to put the csf into practice. Download the quick guide to the nist cybersecurity framework adoption automation tools Web challenges and to make it easier for organizations to use the framework. Approaches, methodologies, implementation guides, mappings to the framework, case studies,. Web acceptable use agreement definition (s): Easily create your business document and get attorney document review for free. Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act (fisma) of 2014, 44 u.s.c.
Acceptable Use Policy Free Template Sample Lawpath
We've generated templates to get you started. Resources include, but are not limited to: Web june 12, 2001 download all papers are copyrighted. These are free to use and fully customizable to your company's it security practices. Web the acceptable use policy template provides a acceptable use policy example stating that internet and social media access and messaging accounts are.
Nist Information Security Policy Template merrychristmaswishes.info
Web nist cybersecurity framework v1.0 (page not in english) (this is a direct translation of version 1.0 of the cybersecurity framework produced by the government. Nist is working with the community to ensure that csf 2.0 is effective for the future. Easily create your business document and get attorney document review for free. Rules of behavior control statement establish and.
Acceptable Use Policy Free Download
Approaches, methodologies, implementation guides, mappings to the framework, case studies,. Download the quick guide to the nist cybersecurity framework adoption automation tools Resources include, but are not limited to: Web the draft update, which nist has released for public comment, reflects changes in the cybersecurity landscape and makes it easier to put the csf into practice. Web acceptable use policy.
How to define an Acceptable Use IT CyberSecurity Standard? Download
Resources include, but are not limited to: Acceptable use of nist information technology resources. Download our acceptable use policy style now. Web the acceptable use policy template provides a acceptable use policy example stating that internet and social media access and messaging accounts are specifically limited to. Teleworkers should ensure that all the devices on their wired and wireless home.
Acceptable Use Policy Template 2019 Policy template, Positive work
Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act (fisma) of 2014, 44 u.s.c. Nist is working with the community to ensure that csf 2.0 is effective for the future. Web this publication is available free of charge from: Web the following guidelines apply to all who use and.
Backup Policy Template Nist
Web acceptable use policies outline what is appropriate and what is inappropriate when it comes to using the organization’s network and the internet. Web acceptable use agreement definition (s): Web users of devices connecting to nist‐guest will require acceptance of access and use rules. Policies belong important components of all security decisions. Nist is working with the community to ensure.
Acceptable Use Policy Template TermsFeed
Web about this sample policy. Web june 12, 2001 download all papers are copyrighted. Acceptable use of nist information technology resources. We've generated templates to get you started. Resources include, but are not limited to:
PPT Information Services Overview PowerPoint Presentation ID278233
Get access to our collection of 2,000+ business & legal document templates. This template can assist an enterprise in developing acceptable use for the cis controls. Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program. Web sans has developed a set of information security policy templates. These.
No Cell Phone Policy At Work Template
Web acceptable use agreement definition (s): Ad make your free online customized information security policy. The access and use rules are presented to the user as follows: Teleworkers should ensure that all the devices on their wired and wireless home. This template can assist an enterprise in developing acceptable use for the cis controls.
Nist Information Security Policy Template merrychristmaswishes.info
Teleworkers should ensure that all the devices on their wired and wireless home. Web the draft update, which nist has released for public comment, reflects changes in the cybersecurity landscape and makes it easier to put the csf into practice. Web sans has developed a set of information security policy templates. Web nist cybersecurity framework v1.0 (page not in english).
Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program. Policies belong important components of all security decisions. Web about this sample policy. Web june 12, 2001 download all papers are copyrighted. Web acceptable use of information technology resource policy access control policy account management/access control standard identification and authentication policy. Whether you need a starting point for developing your first acceptable use policy (aup) or would like to use our template to benchmark your own. Web challenges and to make it easier for organizations to use the framework. These are free to use and fully customizable to your company's it security practices. Nist is working with the community to ensure that csf 2.0 is effective for the future. Easily create your business document and get attorney document review for free. Web policies is important components of all safety decisions. Resources include, but are not limited to: The access and use rules are presented to the user as follows: Web users of devices connecting to nist‐guest will require acceptance of access and use rules. The risk management framework (rmf) provides a process that integrates security, privacy, and cyber supply. Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act (fisma) of 2014, 44 u.s.c. Web acceptable use policy template for the cis controls. This template can assist an enterprise in developing acceptable use for the cis controls. Web sans has developed a set of information security policy templates. Download the quick guide to the nist cybersecurity framework adoption automation tools
Web Acceptable Use Of Information Technology Resource Policy Access Control Policy Account Management/Access Control Standard Identification And Authentication Policy.
The access and use rules are presented to the user as follows: Web june 12, 2001 download all papers are copyrighted. Approaches, methodologies, implementation guides, mappings to the framework, case studies,. Web information security in any organization is largely dependent on the quality of the security policy and the processes that an organization imposes on itself, including policy.
Download The Quick Guide To The Nist Cybersecurity Framework Adoption Automation Tools
We've created templates go get her started. Web acceptable use policies outline what is appropriate and what is inappropriate when it comes to using the organization’s network and the internet. These are free to use and fully customizable to your company's it security practices. Web policies is important components of all safety decisions.
Web Download Our Acceptable Use Policy Template Now.
Web the acceptable use policy template provides a acceptable use policy example stating that internet and social media access and messaging accounts are specifically limited to. Web the draft update, which nist has released for public comment, reflects changes in the cybersecurity landscape and makes it easier to put the csf into practice. This template can assist an enterprise in developing acceptable use for the cis controls. Web challenges and to make it easier for organizations to use the framework.
The Risk Management Framework (Rmf) Provides A Process That Integrates Security, Privacy, And Cyber Supply.
April 2010 author (s) erika mccallister (nist), tim grance (nist), karen scarfone (nist) abstract the purpose of this document is to assist. Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act (fisma) of 2014, 44 u.s.c. Download our acceptable use policy style now. We've generated templates to get you started.